Man in the middle attack (MITM): step by step guide
In this article, we will try to find out the theory of man in the middle attack and some practical points that will help prevent these types of attacks. This will help us understand the risk of such intrusions for our personal lives since MitM attacks allow us to invade communications and listen to our conversations.
Understanding how the internet works
To understand the principle of a man in the middle attack, you should first understand how the Internet itself works. The main points of interaction: clients, routers, servers. The most common client-server communication protocol is the Hypertext Transfer Protocol (HTTP). Surfing the Internet using a browser, email, instant messaging - all this is done through HTTP.
When you enter http://darkhackerworld.com in the address bar of your browser, the client (you) sends a request to display the web page to the server. The packet (HTTP GET request) is transmitted through several routers to the server. After that, the server responds with a web page that is sent to the client and displayed on its monitor. HTTP messages must be sent in a secure manner to ensure confidentiality and anonymity.
Securing communication protocol
A secure communication protocol must have each of the following properties:
1. Privacy - Only the intended recipient can read the message.
2. Authenticity - the identity of the interacting parties is proven.
3. Integrity - confirmation that the message has not been changed in transit.
If at least one of these rules is not observed, the entire protocol is compromised.
HTTP broker attack
An attacker can easily carry out a man in the middle attack using a technique called ARP spoofing. Anyone on your Wi-Fi network can send you a fake ARP packet, because of it you will unconsciously send all your traffic through an attacker instead of a router.
After that, the attacker gains full control over the traffic and can track requests sent to both sides.
To prevent such attacks, a secure version of the HTTP protocol has been created. Transport Layer Security (TLS) and its predecessor, Secure Socket Layer (SSL), are cryptographic protocols that provide secure data transmission over the network. Consequently, the secure protocol will be called HTTPS. You can see how the secure protocol works by typing https://www.darkhackerworld.com in the address bar of your browser (note the presence of S in https). Broker attack on poorly implemented SSLModern SSL uses a good encryption algorithm, but it does not matter if it is implemented incorrectly. If the hacker can intercept the request, he can change it by removing the “S” from the requested URL, thereby bypassing SSL. Such interception and modification of the request can be noticed. For example, if you request https://login.yahoo.com/ and the answer comes http://login.yahoo.com/ this should raise suspicion. At the time of writing, such an attack really works on Yahoo's email service. |
This method of implementing SSL is vulnerable to another type of attack - an attacker creates an SSL connection to the server, but with various tricks forces the user to use HTTP. The above figure shows the attack pattern with HSTS. To prevent such attacks, modern browsers such as Chrome, Firefox, and Tor monitor sites using HSTS and force a client connection to them via SSL. In this case, the attacker conducting the attack on the intermediary will have to create an SSL connection with the victim. |
In order to provide an SLL connection with a user, an attacker must know how to act as a server. Let's look at the technical aspects of SSL.
Understanding SSL
From a hacker's point of view, compromising any communication protocol boils down to finding the weak link among the components listed above (privacy, authenticity, and integrity).SSL uses an asymmetric encryption algorithm. In symmetric encryption, the problem is that the same key is used to encrypt and decrypt data, this approach is unacceptable for Internet protocols since an attacker can trace this key.
Asymmetric encryption includes 2 keys for each side: the public key used for encryption and the confidential key used to decrypt data.
How does SSL provide the three properties required for secure communications?
1. Because asymmetric cryptography is used to encrypt data, SSL provides a private connection. This encryption is not so easy to crack and go unnoticed.
2. The server confirms its legitimacy by sending the client an SSL certificate issued by a certification authority - a trusted third party.
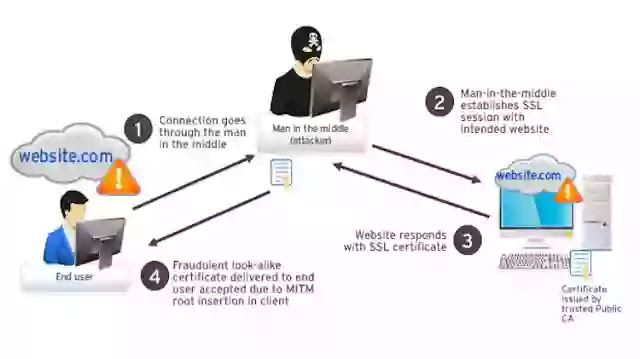
If an attacker somehow manages to obtain a certificate, he can create the conditions for an attack by an intermediary. Thus, he will create 2 connections - with the server and with the victim. The server, in this case, thinks that the attacker is an ordinary client, and the victim does not have the ability to identify the attacker, because the victim provided a certificate proving that he is the server.
Your messages arrive and come in encrypted form, but they go through the chain through the computer of the cybercriminal, where he has full control.
The above figure shows the attack pattern when an attacker has a certificate. The certificate does not have to be tampered with if the attacker has the opportunity to compromise the victim’s browser. In this case, he can insert a self-signed certificate, which will be trusted by default. This is how most intermediary attacks are implemented. In more complex cases, the hacker has to go the other way - to forge a certificate.
Certificate authority issues
The certificate sent by the server is issued and signed by a certification authority. Each browser has a list of trusted certificate authorities, and you can add or remove them. The problem here is that if you decide to remove large centers, you will not be able to visit sites that use certificates signed by these centers.
Certificates and certification authorities have always been the weakest link in an HTTPS connection. Even if everything was implemented correctly and each certification authority has a solid reputation, it is still difficult to come to terms with the fact that many third parties have to be trusted.
Today, there are more than 650 organizations that can issue certificates. If an attacker breaks into any of them, he will get any certificates that he wants.
Even when there was only one certification authority, VeriSign, there was a problem - people who were supposed to prevent reseller attacks were selling interception services.
Also, many certificates were created due to hacking certification authorities. Various tricks and tricks were used to force the attacked user to trust fraudulent certificates.
Forensics
Since an attacker sends fake ARP packets, you cannot see his IP address. Instead, you need to pay attention to the MAC address, which is specific to each device on the network. If you know the MAC address of your router, you can compare it with the MAC address of the default gateway to find out if it is really your router or an attacker.
For example, on Windows, you can use the ipconfig command on the command line (CMD) to see the IP address of your default gateway (last line):
Then use arp -a command to find out the MAC address of this gateway:
But there is another way to notice the attack - if you tracked network activity at the time it started and watched the ARP packets. For example, you can use Wireshark for these purposes, this program will notify you if the MAC address of the default gateway has changed.
Note: if the attacker correctly spoofs MAC addresses, tracing it will be a big problem.
Conclusion
SSL is a protocol that forces an attacker to do a great job to carry out an attack. But it will not protect you from state-sponsored attacks or from qualified hacker organizations.The user's task is to protect their browser and computer to prevent the insertion of a fake certificate (a very common technique). It is also worth paying attention to the list of trusted certificates and removing those that you do not trust.



















0 comments:
Post a Comment