Cybercriminals Are Using Legit Cloud Monitoring Tools As Backdoor
A cybercrime group that has previously struck Docker and Kubernetes cloud environments has evolved to repurpose genuine cloud monitoring tools as a backdoor to carry out malicious attacks, according to new research.
"To our knowledge, this is the first time attackers have been caught using legitimate third party software to target cloud infrastructure," Israeli cybersecurity firm Intezer said in a Tuesday analysis.
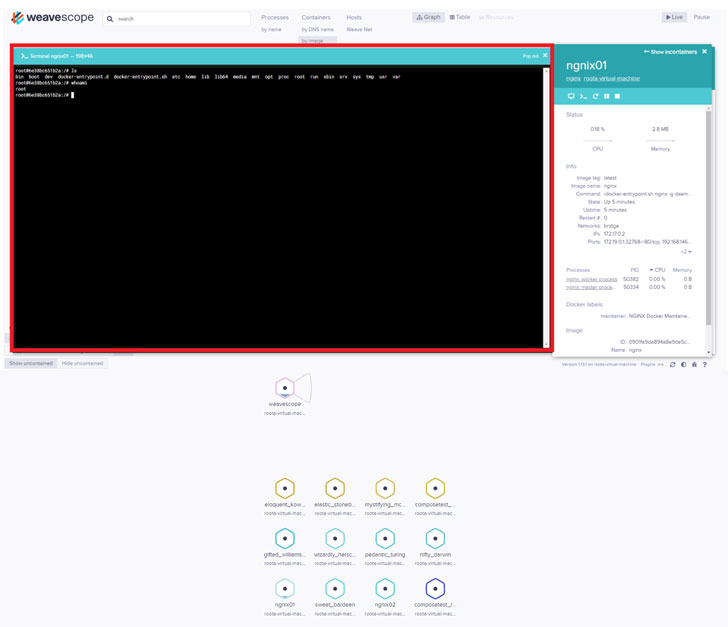
Using software called Weave Scope, which is used as a visualization and monitoring tool for Docker and Kubernetes services, the TeamTNT threat actor not only mapped the cloud environment of their victims but also executed system commands without having to deploy malicious code on the target server explicitly.
TeamTNT has been active at least since late April this year, directing their attacks on misconfigured Docker ports to install a cryptocurrency mining malware and a Distributed Denial-of-Service (DDoS) bot.
Then last month, the crypto-mining gang updated their modus operandi to exfiltrate Amazon Web Services (AWS) logins by scanning the infected Docker and Kubernetes systems for sensitive credential information stored in AWS credentials and config files.
While their method of gaining initial foothold hasn't changed, what has been tweaked is the mode of gaining control over the infected host's infrastructure itself.
Once the attackers found their way in, they set up a new privileged container with a clean Ubuntu image, using it to download and execute cryptominers, gain root access to the server by creating a local privileged user named 'hilde' to connect to the server via SSH, and eventually install Weave Scope.
"By installing a legitimate tool such as Weave Scope the attackers reap all the benefits as if they had installed a backdoor on the server, with significantly less effort and without needing to use malware," Intezer's Nicole Fishbein said.
Although the ultimate goal of TeamTNT appears to be generating cash via cryptocurrency mining, numerous groups that have resorted to deploying cryptojacking worms are successful at compromising enterprise systems in part because of exposed API endpoints, making them an attractive target for cybercriminals.
It's recommended that Docker API endpoints are access restricted to prevent adversaries from taking control over the servers.
"Weave Scope uses default port 4040 to make the dashboard accessible and anyone with access to the network can view the dashboard. Similar to the Docker API port, this port should be closed or restricted by the firewall," the cybersecurity firm said.
"To our knowledge, this is the first time attackers have been caught using legitimate third party software to target cloud infrastructure," Israeli cybersecurity firm Intezer said in a Tuesday analysis.
Using software called Weave Scope, which is used as a visualization and monitoring tool for Docker and Kubernetes services, the TeamTNT threat actor not only mapped the cloud environment of their victims but also executed system commands without having to deploy malicious code on the target server explicitly.
TeamTNT has been active at least since late April this year, directing their attacks on misconfigured Docker ports to install a cryptocurrency mining malware and a Distributed Denial-of-Service (DDoS) bot.
Then last month, the crypto-mining gang updated their modus operandi to exfiltrate Amazon Web Services (AWS) logins by scanning the infected Docker and Kubernetes systems for sensitive credential information stored in AWS credentials and config files.
While their method of gaining initial foothold hasn't changed, what has been tweaked is the mode of gaining control over the infected host's infrastructure itself.
Once the attackers found their way in, they set up a new privileged container with a clean Ubuntu image, using it to download and execute cryptominers, gain root access to the server by creating a local privileged user named 'hilde' to connect to the server via SSH, and eventually install Weave Scope.
"By installing a legitimate tool such as Weave Scope the attackers reap all the benefits as if they had installed a backdoor on the server, with significantly less effort and without needing to use malware," Intezer's Nicole Fishbein said.
Although the ultimate goal of TeamTNT appears to be generating cash via cryptocurrency mining, numerous groups that have resorted to deploying cryptojacking worms are successful at compromising enterprise systems in part because of exposed API endpoints, making them an attractive target for cybercriminals.
It's recommended that Docker API endpoints are access restricted to prevent adversaries from taking control over the servers.
"Weave Scope uses default port 4040 to make the dashboard accessible and anyone with access to the network can view the dashboard. Similar to the Docker API port, this port should be closed or restricted by the firewall," the cybersecurity firm said.
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.










0 comments:
Post a Comment